Key Takeaways
Mobile driver’s licenses (mDLs) and other verifiable digital credentials rely on strong verification models to ensure trust. Verification can happen offline through device-based methods like NFC or QR code scanning, or online through real-time issuer confirmation (server retrieval). Each model has tradeoffs in privacy, accessibility, and compliance with identity verification standards.
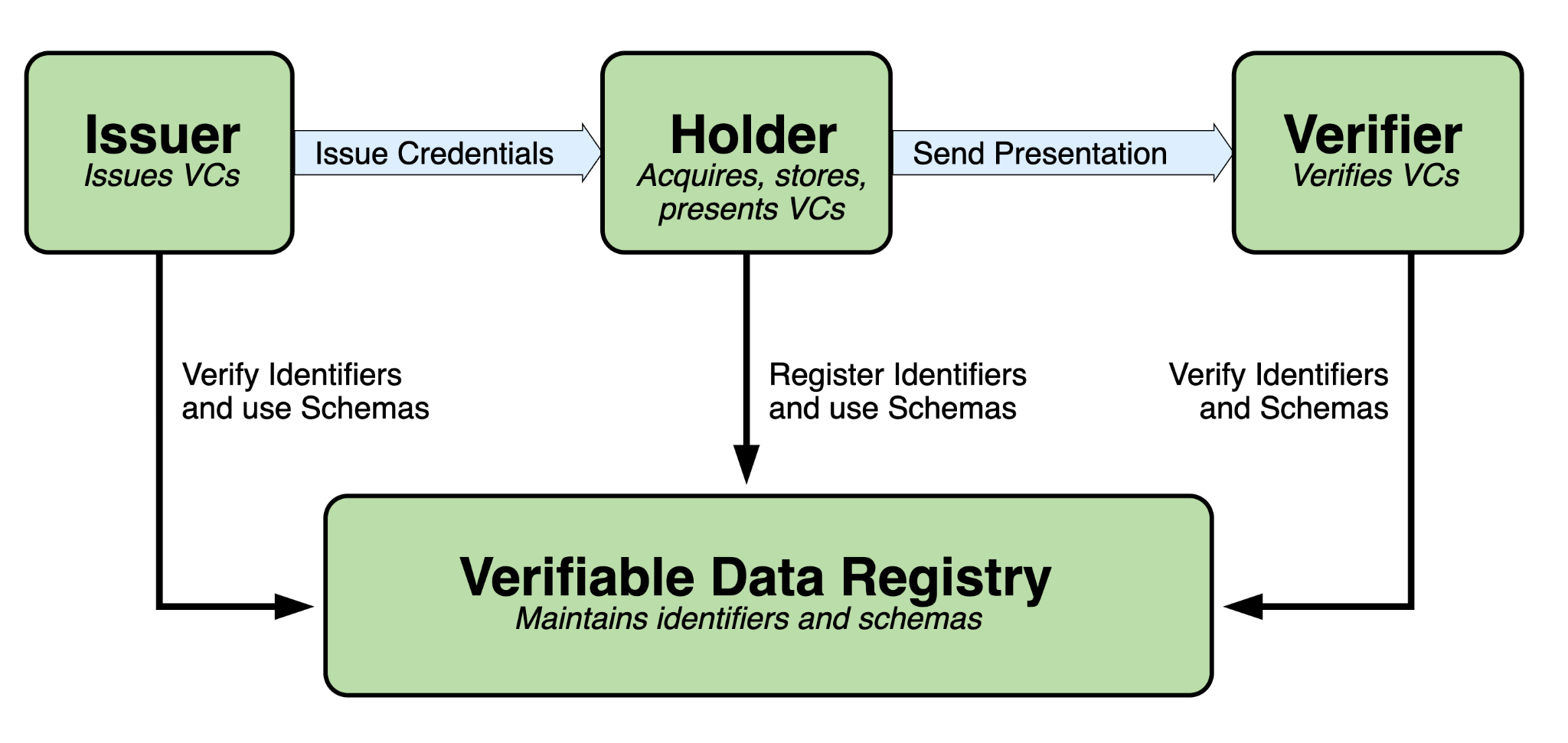
The Three-Party Model
To recap, digital identity systems operate on a three-party model:
- Issuers: Agencies such as DMVs that create and cryptographically sign credentials.
- Holders: Individuals who store credentials in a mobile wallet on their smartphone.
- Verifiers: Entities such as banks, airlines, law enforcement, and employers that confirm authenticity.
This structure ensures scalability and trust across both public and private sectors. Since driver’s licenses in the U.S. are used far beyond driving, verification methods must be reliable in many different scenarios.
Why Verification Matters
Verification proves that a credential is authentic and unaltered. Without it, fraud and counterfeiting could undermine trust in digital identity systems. Verification also determines how much data is shared, which directly affects privacy and compliance obligations.
A strong model must balance:
- Accessibility in both urban and rural settings.
- Security against tampering and counterfeiting.
- Privacy safeguards that prevent oversharing of personal data.
Device Retrieval (Offline Verification)
Offline verification is essential where internet connectivity is limited. Two common methods include:
- NFC technology: Like “Tap to Pay,” an mDL can be tapped against a verifier’s reader. The cryptographic signature built into the credential confirms authenticity.
- QR code scanning: A holder presents a QR code that a verifier scans and validates against preloaded cryptographic data.
Both approaches depend on public key infrastructure (PKI) to confirm integrity and authenticity. Offline models strengthen resilience during natural disasters or emergencies and enable verification in areas without reliable connectivity.
Server Retrieval (Online Verification)
In the online model, the verifier queries the issuer in real time to confirm that the credential is still valid. For example, when a passenger presents an mDL, TSA may contact the DMV to check the status.
Advantages
- Provides the highest level of assurance by confirming status at the exact time of use.
- Supports automated integration into digital workflows.
Risks
- Creates the possibility of surveillance if every verification event is logged.
- Raises compliance issues under regulations like GDPR or CCPA.
Mitigations include selective disclosure, privacy-preserving authentication, and zero-knowledge proofs to limit what data is shared while still confirming validity.
Attended vs. Unattended Interactions
Verification scenarios fall into two categories:
- Attended: In-person checks, such as presenting an mDL at TSA. Standardized in ISO/IEC 18013-5.
- Unattended: Remote interactions, such as submitting an mDL for online banking or job applications. Standardized and outlined in ISO/IEC 18013-7.
Attended interactions benefit from physical context, while unattended interactions rely on digital protocols to ensure security.
Building Trust Across Use Cases
For mDLs and verifiable digital credentials to gain traction, verification must work across contexts:
- Proving age at a bar.
- Passing TSA airport screening.
- Applying for a loan.
- Accessing online government services.
Both device retrieval and server retrieval are needed to cover offline and online use cases. Together, they provide flexibility while balancing usability, privacy, and security.
Final Thoughts
As mobile driver's licenses gain traction, robust verification methods are key to building trust and expanding adoption. The device retrieval model enables offline, cryptographically secure identity checks, while the server retrieval model supports real-time validation when connectivity is available. Both approaches serve important roles, depending on the use case and environment.
By adhering to established standards like ISO/IEC 18013-5 and 18013-7, issuers and verifiers can ensure interoperability across jurisdictions and industries. When combined with privacy-preserving design and clear separation of roles between issuers, holders, and verifiers, these models create a flexible, scalable foundation for verifying identity safely, whether at a traffic stop, a bank branch, or a retail counter.

